Dear Mozilla, of course I learned about your new file sharing project from the news. But it seems that you wanted to be really certain, so today I got this email:
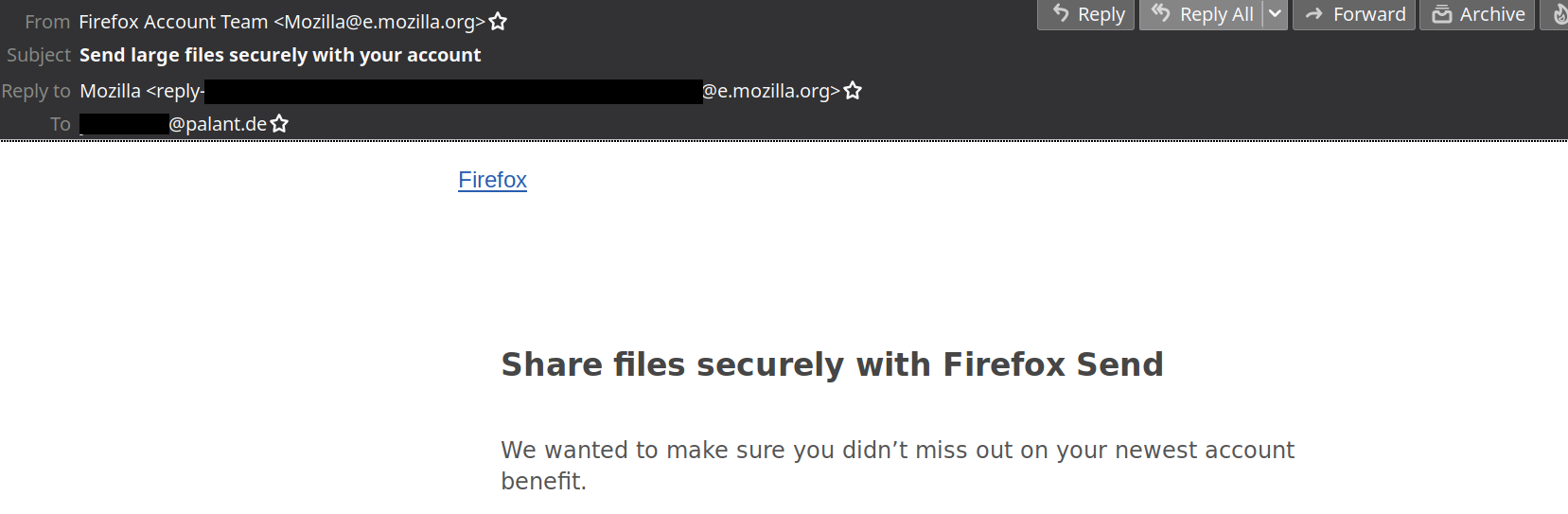
Do you still remember how I opted out of all your emails last year? Luckily, I know that email preferences of all your users are managed via Mozilla Basket and I also know how to retrieve raw data. So here it is:
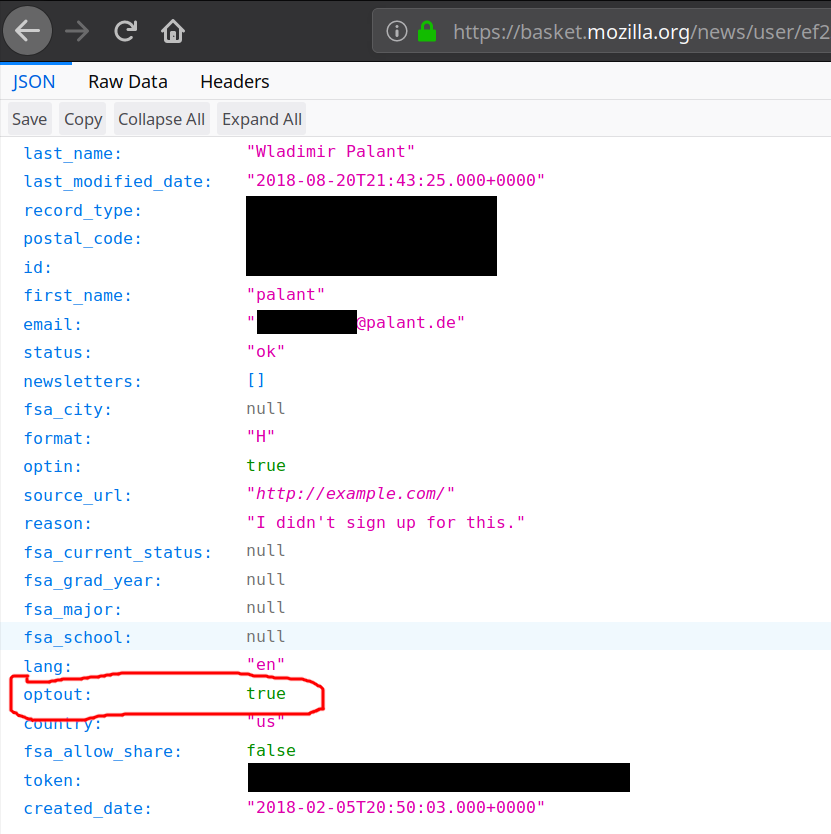
It clearly says that I’ve opted out, so you didn’t forget. So why do you keep sending me promotional messages? Edit (2019-04-05): Yes, that optin value is thoroughly confusing but it doesn’t mean what it seems to mean. Basket only uses it to indicate a “verified email,” somebody who either went through double opt-in once or registered with Firefox Accounts.
This isn’t your only issue however. A year ago I reported a security issue in Mozilla Basket (not publicly accessible). The essence is that subscribing anybody to Mozilla’s newsletters is trivial even if that person opted out previously. The consensus in this bug seems to be that this is “working as expected.” This cannot seriously be it, right?
Now there is some legislation that is IMHO being violated here, e.g. the CAN-SPAM Act and GDPR. And your privacy policy ends with the email address one can contact to report compliance issues. So I did.
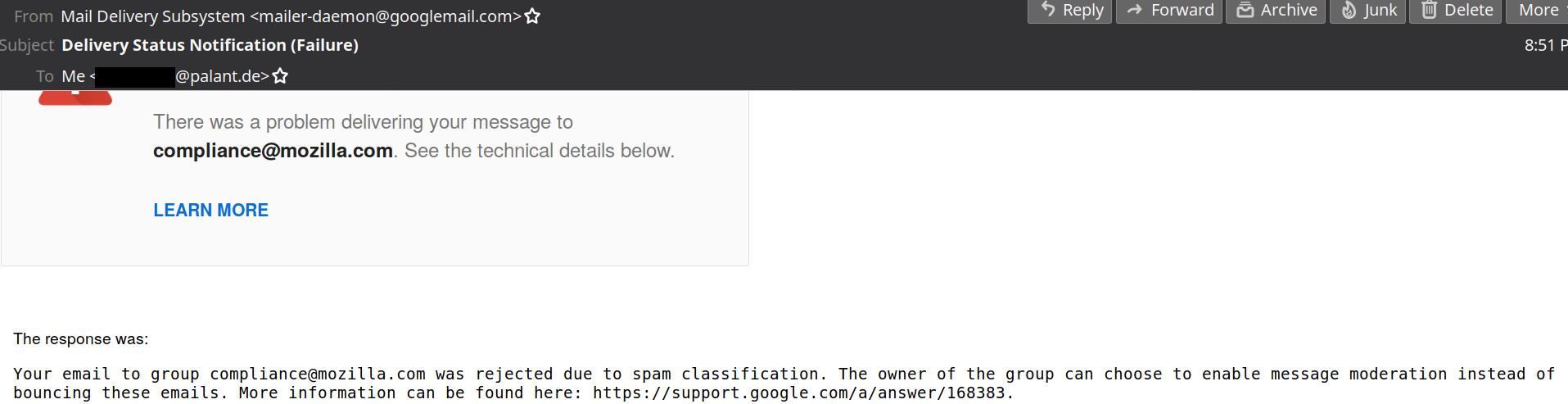
Oh well…
Comments
Oh no, Mozilla. What is you doing?
Maybe you can subscribe compliance@mozilla.com to Mozilla's newsletter? Maybe set up a cron job to do it regularly...
And that's nothing!
7 months ago I opened a bug report to Mozilla describing a wide class of undetectable attacks that can be carried through JavaScript, targetting either a specific person or a small group (identified though the same techniques used to personalize ads) and covered though HTTP Cache Control.
A couple of PoC exploits showed how such attacks can be used to tunnel into any private network behind corporate firewall and proxies (see here and here)
These attacks are currently being exploited in the wide. The Russian Government was caught to use it to build a database of their citizens that use security tools: https://bugzilla.mozilla.org/show_bug.cgi?id=1487081#c16 (be careful where you click or you might be profiled too).
Yet, according to Mozilla (and Google)
I mean, wasn't Firefox "Made for people, not profit."
Trouble is: we want websites to have dynamic behavior, so dynamic behavior we get. The good news is: the web applications that the Russian script there is fingerprinting, can easily prevent this kind of attack. But there are plenty of other applications which actually want to be accessible to websites while running on localhost. As far as fingerprinting goes, this certainly isn't the worst issue out there.
Also, the IP address scanning script by rain-1 isn't working well. If you want to see really scary stuff, search for DNS rebinding. These attacks have been discussed for more than a decade, yet preventing them without breaking the web as a whole is difficult to impossible.
Finally, I don't think that you are correct when you say "undetectable." These attacks can very well be detected, both by the user and the target. Attribution is also possible, via various HTTP headers. Which is probably why they are so uncommon in the wild.
I'd suggest that —due to GDPR and friends— they've switched from opt-out to opt-in. See the "optin" key.
Just a guess. Doesn't explain how it got set.
Things aren't always what they appear to be. :-)
The "optin" key actually indicates that the email address is verified, so no confirmation email is necessary. It's either set if you do the double opt-in dance once or if you are signed up with Firefox Accounts. In my case it was the latter.
There's an "optin" flag set in the response as well. Maybe there are conflicting options saved for your account?
Never attribute to malice what could be an accident.
Nope, it's only a confusing name. The "optin" key should have really been "verifiedemail" key. It's either set if you do the double opt-in dance once or if you are signed up with Firefox Accounts. In my case it was the latter.